# Run at 5/12/2024 12:01:08 PM
# KpRm (Kernel-panik) version 2.17.0
# Website https://kernel-panik.me/tool/kprm/
# Run by localAdmin from C:\Users\lim1\Desktop
# Computer Name: HP2024
# OS: Windows 11 X64 (22631) (10.0.22631.3447)
# Number of passes: 2
- Checked options -
~ Registry Backup
~ Delete Tools
~ Restore System Settings
~ UAC Restore
~ Delete Restore Points
~ Create Restore Point
~ Delete Quarantines
- Create Registry Backup -
~ [OK] Hive C:\windows\System32\config\SOFTWARE backed up
~ [OK] Hive C:\Users\localAdmin\NTUSER.dat backed up
[OK] Registry Backup: \KPRM\backup\2024-05-12-12-01-08
- Delete Tools -
No tools found
- Restore System Settings -
[OK] Reset WinSock
[OK] FLUSHDNS
[OK] Hide Hidden file.
[OK] Show Extensions for known file types
[OK] Hide protected operating system files
- Restore UAC -
[OK] Set EnableLUA with default (1) value
[OK] Set ConsentPromptBehaviorAdmin with default (5) value
[OK] Set ConsentPromptBehaviorUser with default (3) value
[OK] Set EnableInstallerDetection with default (0) value
[OK] Set EnableSecureUIAPaths with default (1) value
[OK] Set EnableUIADesktopToggle with default (0) value
[OK] Set EnableVirtualization with default (1) value
[OK] Set FilterAdministratorToken with default (0) value
[OK] Set PromptOnSecureDesktop with default (1) value
[OK] Set ValidateAdminCodeSignatures with default (0) value
- Clear Restore Points -
~ [OK] RP named KpRm created at 05/12/2024 13:38:43 deleted
[OK] All system restore points have been successfully deleted
- Create Restore Point -
[OK] System Restore Point created
- Display System Restore Point -
~ RP named KpRm created at 05/12/2024 16:01:59
-- KPRM finished in 73.57s --
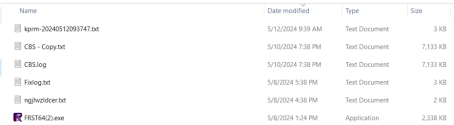
And these (in screenshot below) are the files from the fixes still showing on my desktop after running the tool --
KPRM wrote the log to a folder on C , KPRM which is why I could not find it before.
I had to sign out of the Limited account again after running the tool, I think this has something to do with the LocalAdmin account not being able to access the LImited account folder - I am given the option to change that but I have been keeping it that way.
Sorry about being confusing!! I am confused myself... sorry...

# KpRm (Kernel-panik) version 2.17.0
# Website https://kernel-panik.me/tool/kprm/
# Run by localAdmin from C:\Users\lim1\Desktop
# Computer Name: HP2024
# OS: Windows 11 X64 (22631) (10.0.22631.3447)
# Number of passes: 2
- Checked options -
~ Registry Backup
~ Delete Tools
~ Restore System Settings
~ UAC Restore
~ Delete Restore Points
~ Create Restore Point
~ Delete Quarantines
- Create Registry Backup -
~ [OK] Hive C:\windows\System32\config\SOFTWARE backed up
~ [OK] Hive C:\Users\localAdmin\NTUSER.dat backed up
[OK] Registry Backup: \KPRM\backup\2024-05-12-12-01-08
- Delete Tools -
No tools found
- Restore System Settings -
[OK] Reset WinSock
[OK] FLUSHDNS
[OK] Hide Hidden file.
[OK] Show Extensions for known file types
[OK] Hide protected operating system files
- Restore UAC -
[OK] Set EnableLUA with default (1) value
[OK] Set ConsentPromptBehaviorAdmin with default (5) value
[OK] Set ConsentPromptBehaviorUser with default (3) value
[OK] Set EnableInstallerDetection with default (0) value
[OK] Set EnableSecureUIAPaths with default (1) value
[OK] Set EnableUIADesktopToggle with default (0) value
[OK] Set EnableVirtualization with default (1) value
[OK] Set FilterAdministratorToken with default (0) value
[OK] Set PromptOnSecureDesktop with default (1) value
[OK] Set ValidateAdminCodeSignatures with default (0) value
- Clear Restore Points -
~ [OK] RP named KpRm created at 05/12/2024 13:38:43 deleted
[OK] All system restore points have been successfully deleted
- Create Restore Point -
[OK] System Restore Point created
- Display System Restore Point -
~ RP named KpRm created at 05/12/2024 16:01:59
-- KPRM finished in 73.57s --
And these (in screenshot below) are the files from the fixes still showing on my desktop after running the tool --
KPRM wrote the log to a folder on C , KPRM which is why I could not find it before.
I had to sign out of the Limited account again after running the tool, I think this has something to do with the LocalAdmin account not being able to access the LImited account folder - I am given the option to change that but I have been keeping it that way.
Sorry about being confusing!! I am confused myself... sorry...


Last edited:


