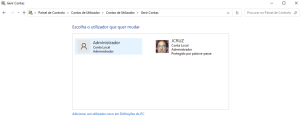
Hi, DR M, thanks for your support, here is the content of profile.txt and the two screenshots.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList]
"Default"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,44,00,72,00,69,00,\
76,00,65,00,25,00,5c,00,55,00,73,00,65,00,72,00,73,00,5c,00,44,00,65,00,66,\
00,61,00,75,00,6c,00,74,00,00,00
"ProfilesDirectory"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,44,00,72,\
00,69,00,76,00,65,00,25,00,5c,00,55,00,73,00,65,00,72,00,73,00,00,00
"ProgramData"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,44,00,72,00,69,\
00,76,00,65,00,25,00,5c,00,50,00,72,00,6f,00,67,00,72,00,61,00,6d,00,44,00,\
61,00,74,00,61,00,00,00
"Public"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,44,00,72,00,69,00,76,\
00,65,00,25,00,5c,00,55,00,73,00,65,00,72,00,73,00,5c,00,50,00,75,00,62,00,\
6c,00,69,00,63,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-18]
"Flags"=dword:0000000c
"ProfileImagePath"=hex(2):25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,\
00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,\
5c,00,63,00,6f,00,6e,00,66,00,69,00,67,00,5c,00,73,00,79,00,73,00,74,00,65,\
00,6d,00,70,00,72,00,6f,00,66,00,69,00,6c,00,65,00,00,00
"RefCount"=dword:00000001
"Sid"=hex:01,01,00,00,00,00,00,05,12,00,00,00
"State"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-19]
"Flags"=dword:00000000
"ProfileImagePath"=hex(2):25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,\
00,6f,00,74,00,25,00,5c,00,53,00,65,00,72,00,76,00,69,00,63,00,65,00,50,00,\
72,00,6f,00,66,00,69,00,6c,00,65,00,73,00,5c,00,4c,00,6f,00,63,00,61,00,6c,\
00,53,00,65,00,72,00,76,00,69,00,63,00,65,00,00,00
"State"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-20]
"Flags"=dword:00000000
"ProfileImagePath"=hex(2):25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,\
00,6f,00,74,00,25,00,5c,00,53,00,65,00,72,00,76,00,69,00,63,00,65,00,50,00,\
72,00,6f,00,66,00,69,00,6c,00,65,00,73,00,5c,00,4e,00,65,00,74,00,77,00,6f,\
00,72,00,6b,00,53,00,65,00,72,00,76,00,69,00,63,00,65,00,00,00
"State"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-3653589094-3565606866-458211961-1001]
"ProfileImagePath"=hex(2):43,00,3a,00,5c,00,55,00,73,00,65,00,72,00,73,00,5c,\
00,55,00,74,00,69,00,6c,00,69,00,7a,00,61,00,64,00,6f,00,72,00,00,00
"Flags"=dword:00000000
"FullProfile"=dword:00000001
"State"=dword:00000100
"Sid"=hex:01,05,00,00,00,00,00,05,15,00,00,00,66,58,c5,d9,d2,d7,86,d4,79,c2,4f,\
1b,e9,03,00,00
"LocalProfileLoadTimeLow"=dword:c46aac26
"LocalProfileLoadTimeHigh"=dword:01d8856a
"ProfileAttemptedProfileDownloadTimeLow"=dword:00000000
"ProfileAttemptedProfileDownloadTimeHigh"=dword:00000000
"ProfileLoadTimeLow"=dword:00000000
"ProfileLoadTimeHigh"=dword:00000000
"LocalProfileUnloadTimeLow"=dword:886eaf09
"LocalProfileUnloadTimeHigh"=dword:01d8803c
"RunLogonScriptSync"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-3653589094-3565606866-458211961-1002]
"ProfileImagePath"=hex(2):43,00,3a,00,5c,00,55,00,73,00,65,00,72,00,73,00,5c,\
00,6a,00,63,00,72,00,75,00,7a,00,00,00
"Flags"=dword:00000000
"FullProfile"=dword:00000001
"State"=dword:00000204
"Sid"=hex:01,05,00,00,00,00,00,05,15,00,00,00,66,58,c5,d9,d2,d7,86,d4,79,c2,4f,\
1b,ea,03,00,00
"LocalProfileLoadTimeLow"=dword:a36277d8
"LocalProfileLoadTimeHigh"=dword:01d73c05
"ProfileAttemptedProfileDownloadTimeLow"=dword:00000000
"ProfileAttemptedProfileDownloadTimeHigh"=dword:00000000
"ProfileLoadTimeLow"=dword:00000000
"ProfileLoadTimeHigh"=dword:00000000
"RunLogonScriptSync"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-3653589094-3565606866-458211961-500]
"ProfileImagePath"=hex(2):43,00,3a,00,5c,00,55,00,73,00,65,00,72,00,73,00,5c,\
00,41,00,64,00,6d,00,69,00,6e,00,69,00,73,00,74,00,72,00,61,00,64,00,6f,00,\
72,00,00,00
"Flags"=dword:00000000
"FullProfile"=dword:00000001
"State"=dword:00000100
"Sid"=hex:01,05,00,00,00,00,00,05,15,00,00,00,66,58,c5,d9,d2,d7,86,d4,79,c2,4f,\
1b,f4,01,00,00
"LocalProfileLoadTimeLow"=dword:3377aa71
"LocalProfileLoadTimeHigh"=dword:01d88566
"ProfileAttemptedProfileDownloadTimeLow"=dword:00000000
"ProfileAttemptedProfileDownloadTimeHigh"=dword:00000000
"ProfileLoadTimeLow"=dword:00000000
"ProfileLoadTimeHigh"=dword:00000000
"RunLogonScriptSync"=dword:00000000
"LocalProfileUnloadTimeLow"=dword:2e39e3be
"LocalProfileUnloadTimeHigh"=dword:01d88566